Generate An Encrypted Key File For Veracrypt
VeraCrypt is free open-source disk encryption software for Windows, Mac OS X and Linux. In case an attacker forces you to reveal the password, VeraCrypt provides plausible deniability. In contrast to file encryption, data encryption performed by VeraCrypt is real-time (on-the-fly), automatic, transparent, needs very little memory, and does not involve temporary unencrypted files.
2fa key fob. Protect your digital world with YubiKey. Stop account takeovers, go passwordless and modernize your multifactor authentication. Get the world’s leading security key for superior security, user experience and return on investment. Mar 23, 2020 These devices are small, like a key fob and produce a unique numeric code every few minutes. After the initial request to access a certain set of data is received, the system requires a second authentication which corresponds to the code displayed on the fob. This can be a costly method of 2FA, depending on the size of the business. Jan 14, 2017 By Paul Wagenseil 14 January 2017 It's not hard to cheaply make your own two-factor authentication USB key, a researcher showed at the ShmooCon hacker conference. Two Factor Authentication (2FA or TFA) is the technical term for the process of requiring a user to verify their identity in two unique ways before they are granted access to the system. Traditionally, users have relied on and are accustomed to authentication systems that require them to provide. Feb 22, 2019 The best security key for most people: YubiKey 5 NFC. Yubico’s YubiKey 5 NFC — which uses both a USB-A connector and wireless NFC — is the best key for logging into your online accounts.
If verification is successfully completed with Equifax, but not with Experian and/or TransUnion, as applicable, you will not receive Credit Features from such bureau(s) until the verification process is successfully completed and until then you will only receive Credit Features from Equifax. If your plan also includes Credit Features from Experian and/or TransUnion, the above verification process must also be successfully completed with Experian and/or TransUnion, as applicable. Norton product key generator online. Any credit monitoring from Experian and TransUnion will take several days to begin after your successful plan enrollment.
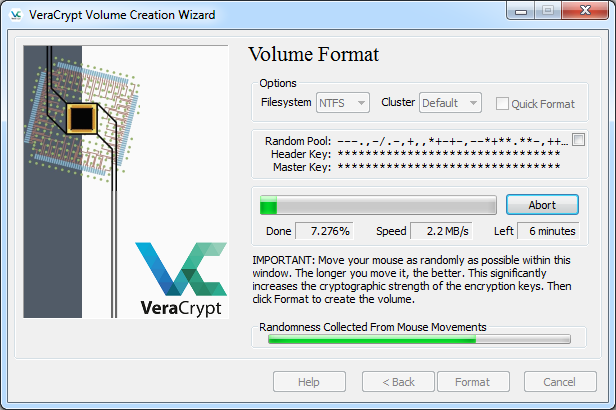
VeraCrypt keyfile is a file whose content is combined with a password. The user can use any kind of file as a VeraCrypt keyfile. The user can also generate a keyfile using the built-in keyfile generator, which utilizes the VeraCrypt RNG to generate a file with random content (for more information, see the section Random Number Generator).
Nov 15, 2018 VeraCrypt is a disk encryption utility that allows you to encrypt an entire disk, a partition on the disk or create a virtual disk (file container). The only way you could email the document encrypted in VeraCrypt is to create a file container, place your document in the mounted file container, dismount the file container and email the file. Aug 11, 2017 Losing your USB drive can be a disaster, but keep your data safe with Windows, macOS and Linux with VeraCrypt. For the article go to: https://www.maketecheas. Nobody can steal/read/edit your data on the encrypted volume without using the correct password/keyfile(s). The entire filesystem will be encrypted including file names, folder names, contents of every file, free space, meta data, etc. You can store files on.
The maximum size of a keyfile is not limited; however, only its first 1,048,576 bytes (1 MB) are processed (all remaining bytes are ignored due to performance issues connected with processing extremely large files). The user can supply one or more keyfiles (the number of keyfiles is not limited).
Keyfiles can be stored on PKCS-11-compliant [23] security tokens and smart cards protected by multiple PIN codes (which can be entered either using a hardware PIN pad or via the VeraCrypt GUI).
Keyfiles are processed and applied to a password using the following method:
- Let P be a VeraCrypt volume password supplied by user (may be empty)
- Let KP be the keyfile pool
- Let kpl be the size of the keyfile pool KP, in bytes (64, i.e., 512 bits);
kpl must be a multiple of the output size of a hash function H
- Let pl be the length of the password P, in bytes (in the current version: 0 ≤pl ≤ 64)
- if kpl > pl, append (kpl – pl) zero bytes to the passwordP (thus pl = kpl)
- Fill the keyfile pool KP with kpl zero bytes.
- For each keyfile perform the following steps:
- Set the position of the keyfile pool cursor to the beginning of the pool
- Initialize the hash function H
- Load all bytes of the keyfile one by one, and for each loaded byte perform the following steps:
- Hash the loaded byte using the hash function H without initializing the hash, to obtain an intermediate hash (state)M. Do not finalize the hash (the state is retained for next round).
- Divide the state M into individual bytes.
For example, if the hash output size is 4 bytes, (T0T1T2T3) = M - Write these bytes (obtained in step 7.c.ii) individually to the keyfile pool with the modulo 28 addition operation (not by replacing the old values in the pool) at the position of the pool cursor. After a byte is written, the pool cursor position is advanced by one byte. When the cursor reaches the end of the pool, its position is set to the beginning of the pool.
- Apply the content of the keyfile pool to the password P using the following method:
- Divide the password P into individual bytes B0..Bpl-1.
Note that if the password was shorter than the keyfile pool, then the password was padded with zero bytes to the length of the pool in Step 5 (hence, at this point the length of the password is always greater than or equal to the length of the keyfile pool). - Divide the keyfile pool KP into individual bytes G0..Gkpl-1
- For 0 ≤ i < kpl perform: Bi = Bi ⊕ Gi
- P = B0B1 .. Bpl-2Bpl-1
- Divide the password P into individual bytes B0..Bpl-1.
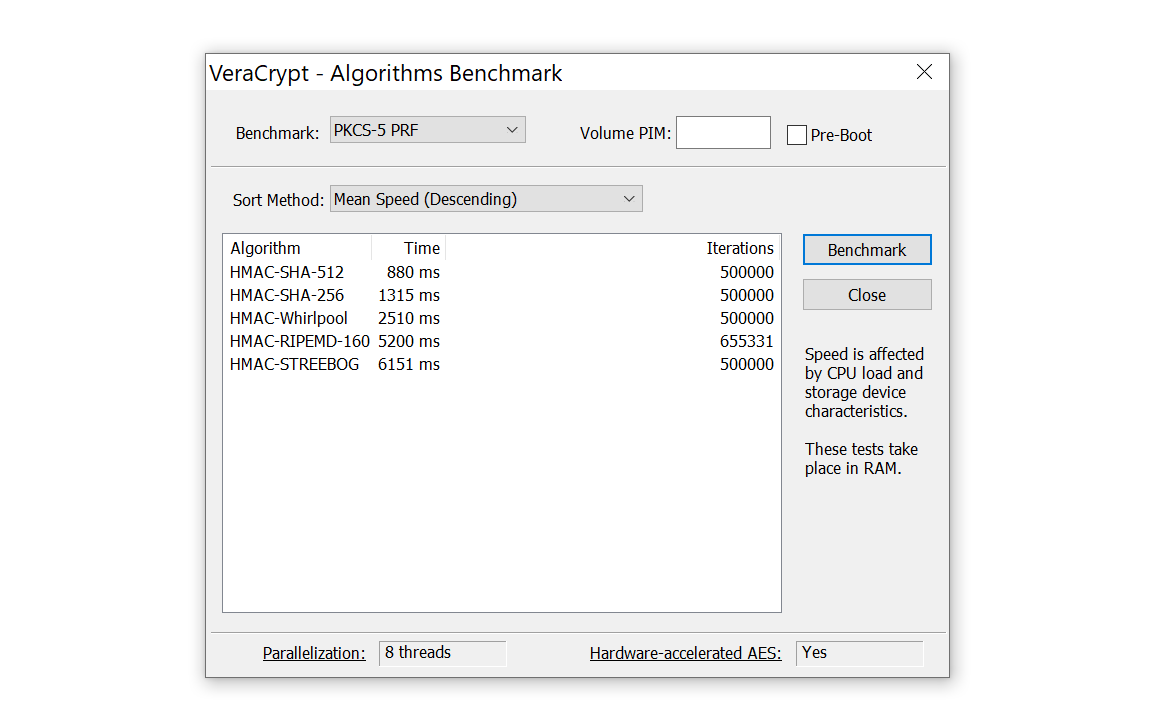
- The password P (after the keyfile pool content has been applied to it) is now passed to the header key derivation function PBKDF2 (PKCS #5 v2), which processes it (along with salt and other data) using a cryptographically secure hash algorithm selected by the user (e.g., SHA-512). See the section Header Key Derivation, Salt, and Iteration Count for more information.
Key File To Ppt
How To Open Veracrypt File
The role of the hash function H is merely to perform diffusion [2]. CRC-32 is used as the hash functionH. Note that the output of CRC-32 is subsequently processed using a cryptographically secure hash algorithm: The keyfile pool content (in addition to being hashed using CRC-32) is applied to the password, which is then passed to the header key derivation function PBKDF2 (PKCS #5 v2), which processes it (along with salt and other data) using a cryptographically secure hash algorithm selected by the user (e.g., SHA-512). The resultant values are used to form the header key and the secondary header key (XTS mode).