Generate Key.json For User Gcloud Cli
Groundbreaking solutions. Transformative know-how. Whether your business is early in its journey or well on its way to digital transformation, Google Cloud's solutions and technologies help chart a path to success. NAME create-service-key - Create key for a service instance USAGE cf create-service-key SERVICEINSTANCE SERVICEKEY -c PARAMETERSASJSON Optionally provide service-specific configuration parameters in a valid JSON object in-line. Hopefully, this nice trick can speed up your build environments by not having to maintain steps to install and configure the gcloud CLI. This is not the only way to authenticate to GKE clusters without gcloud. You can also use Kubernetes service accounts to authenticate as well, perhaps we can explore this in another article. How to generate a JSON Web Key (JWK) JSON Web Keys. To generate an OKP JWK just specify the name of the Edwards curve and any key metadata required by your. I've spent already several hours with this problem but it seems that I can't activate a service account to develop locally an App Engine project (If I deploy teh project it authenticates well since.
- Generate Key.json For User Gcloud Clinton
- Install Gcloud Sdk
- Generate Key.json For User Gcloud Cli Windows 10
- Generate Key.json For User Gcloud Cli Password
The gcloud compute command-line tool enables us to easily manage our Google Compute Engine resources in a friendlier format than using the Compute Engine API. Google Compute Engine uses OAuth2 to authenticate and authorize access. Before we can use gcloud compute, we must first authorize the Cloud. All of Us Researcher Workbench. Contribute to all-of-us/workbench development by creating an account on GitHub.
Terraform Cloud has three workflows for managing Terraform runs.
- The UI/VCS-driven run workflow, which is the primary mode of operation.
- The API-driven run workflow, which is more flexible but requires you to create some tooling.
- The CLI-driven run workflow described below, which uses Terraform's standard CLI tools to execute runs in Terraform Cloud.
» Summary
The Terraform remote backend brings Terraform Cloud's collaboration features into the familiar Terraform CLI workflow. It offers the best of both worlds to developers who are already comfortable with using Terraform, and can work with existing CI/CD pipelines.
Users can start runs with the standard terraform plan and terraform apply commands, and can watch the progress of the run without leaving their terminal. These runs execute remotely in Terraform Cloud; they use variables from the appropriate workspace, enforce any applicable Sentinel policies, and can access Terraform Cloud's private module registry and remote state inputs.
Terraform Cloud offers two kinds of CLI-driven runs, to support different stages of your workflow:
terraform planstarts a speculative plan in a Terraform Cloud workspace, using configuration files from a local directory. Developers can quickly check the results of edits (including compliance with Sentinel policies) without needing to copy sensitive variables to their local machine.
Speculative plans work with all workspaces, and can co-exist with the VCS-driven workflow.
RXKFJ-67HBV-84TD2-RMDK8-9BDMT. 4FWCC-M3XVT-GQVVC-MKQYG-HP7YB. 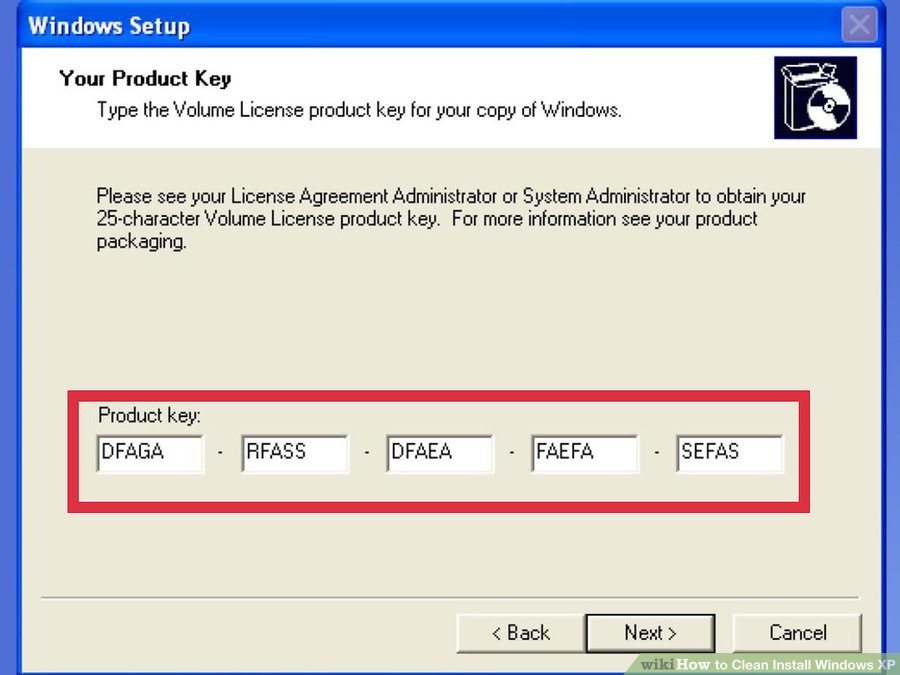 G2JMP-2PC7G-RYBYX-PPF38-3KKTY. HBJFW-XJ7K3-34JDX-VPPTW-227G6.
G2JMP-2PC7G-RYBYX-PPF38-3KKTY. HBJFW-XJ7K3-34JDX-VPPTW-227G6.
terraform applystarts a normal plan and apply in a Terraform Cloud workspace, using configuration files from a local directory.
Remote terraform apply is for workspaces without a linked VCS repository. It replaces the VCS-driven workflow with a more traditional CLI workflow.
To supplement these remote operations, you can also use the optional Terraform Enterprise Provider, which interacts with the resources supported by Terraform Cloud. It can be useful for editing variables and workspace settings through the Terraform CLI.
» Remote Backend Configuration
To configure the remote backend, a stanza needs to be added to the Terraform configuration. It must specify the remote backend, the name of a Terraform Cloud organization, and the workspace(s) to use. The example below uses one workspace; see the remote backend documentation for more details.
Next, run terraform login to authenticate with Terraform Cloud. Alternatively, you can manually configure credentials in the CLI config file.
The backend can be initialized with terraform init.
» Implicit Workspace Creation
If you configure the remote backend to use a workspace that doesn't yet exist in your organization, Terraform Cloud will create a new workspace with that name when you run terraform init. The output of terraform init will inform you when this happens.
Now, Windows 10 Crack as well as its Store. From where you can download different applications.Key Features Of Windows 10 Crack:. More, it is fast, safe, and easy to use than the preceding versions. It is the newest edition of Windows by Microsoft. Windows 10 generated product key mac. And you will be allowed to use all of them just right after you install windows.
Automatically created workspaces might not be immediately ready to use, so use Terraform Cloud's UI to check a workspace's settings and data before performing any runs. In particular, note that:
- No Terraform variables or environment variables are created by default. Terraform Cloud will use
*.auto.tfvarsfiles if they are present, but you will usually still need to set some workspace-specific variables. - The execution mode defaults to 'Remote,' so that runs occur within Terraform Cloud's infrastructure instead of on your workstation.
- New workspaces are not automatically connected to a VCS repository, and do not have a working directory specified.
- A new workspace's Terraform version defaults to the most recent release of Terraform at the time the workspace was created.
» Variables in CLI-Driven Runs
Remote runs in Terraform Cloud use variables from two sources:
- Terraform variables and environment variables set in the workspace. These can be edited via the UI, the API, or the
tfeTerraform provider. - Terraform variables from any
*.auto.tfvarsfiles included in the configuration. Workspace variables, if present, override these.
Note: Remote runs do not use environment variables from your shell environment, and do not support specifying variables (or .tfvars files) as command line arguments.
» Remote Working Directories
If you manage your Terraform configurations in self-contained repositories, the remote working directory always has the same content as the local working directory.
If you use a combined repository and specify a working directory on workspaces, you can run Terraform from either the real working directory or from the root of the combined configuration directory. In both cases, Terraform will upload the entire combined configuration directory.
» Excluding Files from Upload
Version note:.terraformignore support was added in Terraform 0.12.11.
Generate Key.json For User Gcloud Clinton
CLI-driven runs upload an archive of your configuration directoryto Terraform Cloud. If the directory contains files you want to exclude from upload,you can do so by defining a .terraformignore file in your configuration directory.
» Remote Speculative Plans
Install Gcloud Sdk
To run a speculative plan on your configuration, use the terraform plan command. The plan will run in Terraform Cloud, and the logs will stream back to the command line along with a URL to view the plan in the Terraform Cloud UI.
Users can run speculative plans in any workspace where they have plan access.
Speculative plans use the configuration code from the local working directory, but will use variable values from the specified workspace.
» Remote Applies
Generate Key.json For User Gcloud Cli Windows 10
When configuration changes are ready to be applied, use the terraform apply command. The apply will start in Terraform Cloud, and the command line will prompt for approval before applying the changes.
Remote applies require write access to the workspace.
Remote applies use the configuration code from the local working directory, but will use variable values from the specified workspace.
Important: You cannot run remote applies in workspaces that are linked to a VCS repository, since the repository serves as the workspace’s source of truth. To apply changes in a VCS-linked workspace, merge your changes to the designated branch.
» Sentinel Policies
Generate Key.json For User Gcloud Cli Password
If the specified workspace uses Sentinel policies, those policies will run against all speculative plans and remote applies in that workspace. The policy output will be available in the terminal. Hard mandatory checks cannot be overridden and they prevent terraform apply from applying changes.